Remote attestation has been a technology around for decades now. Richard Stallman railed about the freedom it would take in 2005, A Senator presented a bill asking for the required chips to become mandatory, and Microsoft prepared Palladium to improve “security” and bring remote attestation (among other things) to the masses. Then it all fell apart – Palladium was canceled, a Senator retired, and TPM chips have been in our PCs for years but have generally been considered benign.
For those who do not know what remote attestation is:
- Remote attestation lets an external system validate, cryptographically, certain properties about a device.
- For example, proving to a remote system that Secure Boot is enabled on your Windows PC, with no ability to forge that proof. And by extension, potentially loading a kernel driver that can prove certain installed applications have not been tampered with.
- TPM chips invented in ~2004 were widely feared because they enabled this capability, but until now they have been primarily used only in corporate networks and for BitLocker hard drive encryption.
When it was first invented, it was widely feared by Linux users and by Richard Stallman, especially after Secure Boot was rolled out. Could an internet network require that users run up-to-date Windows, with Secure Boot on, and thus completely lock out Linux or anyone who is running Windows in a way Microsoft does not intend? With remote attestation, absolutely.
In practice though, only corporate networks adopted remote attestation to join, and only on their business PCs through the TPM chip (no BYOD here). TPMs have a ludicrous amount of certificates needing trusting, many in different formats and algorithms (1,681 right now, to be exact), and almost everything that isn’t a PC doesn’t have a TPM. Because of that, building a remote attestation setup with support for a broad variety of devices was, and is, very difficult. Easy for a business with a predictable fleet on one platform, almost impossibly complicated for the random assortment of general devices. And so, the threat of the TPM and remote attestation in general was dismissed as being fearmongering from 2 decades ago that never became reality.
If only it stayed that way. Remote Attestation is coming back and is, in my opinion, a legitimate threat to user freedom once more, and almost nobody has noticed. Not even on Hacker News or Linux circles like Phoronix where many such new technologies and changes are discussed.
Consider in the past few years:
- Why is Microsoft building their own chip, the Pluton, into new Intel, AMD, and Qualcomm processors? Why does it matter so much to add a unified root of trust to the Windows PC?
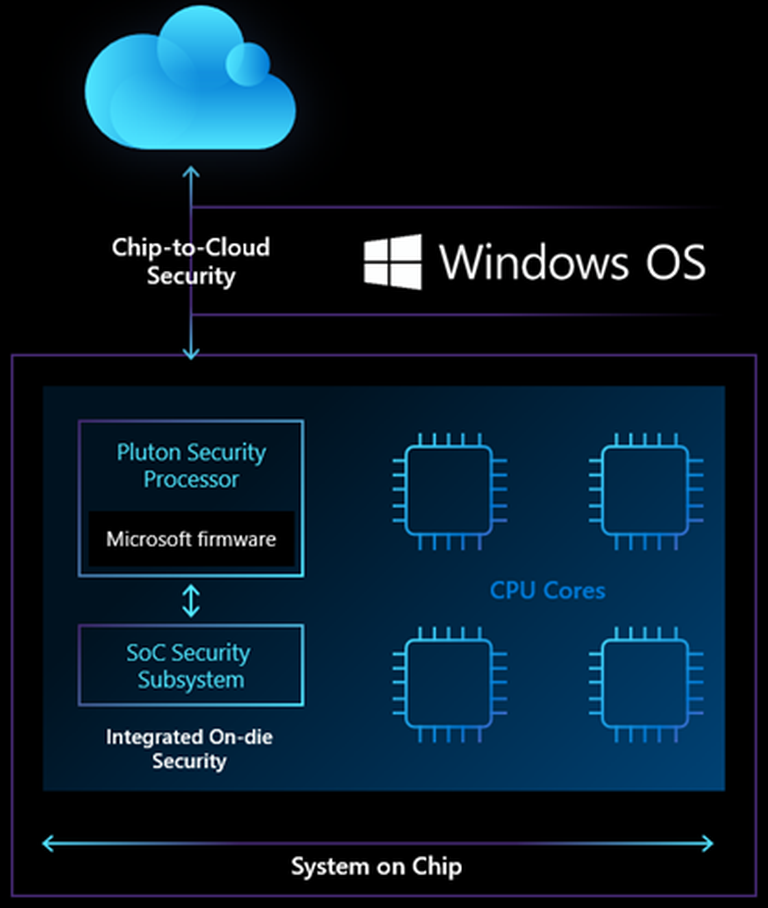
- Why does Windows 11 require a TPM 2.0 module?
- Why has every PC since 2016 been mandated to have TPM 2.0 installed and enabled?
- Why do so many apps on Android, from banking apps to McDonalds, now require SafetyNet checks to ensure your device hasn’t been rooted?

- What’s with some new video games requiring TPM and Secure Boot on Windows 11?
Remember that remote attestation has been possible for decades, but was overly complicated, unsupported on many devices, and just not practical outside of corporate networks. But in the last few years, things have changed.
- What was once a fraction of PCs with TPMs, is now approaching 100% because of the 2016 requirement change, and because of the Windows 11 mandate. In ~5 more years, almost all consumer PCs will have a TPM installed.
- macOS and iOS added attestation already with the DeviceCheck framework in iOS 11 / macOS 10.15. They don’t use a TPM but instead use the Secure Enclave from the T2 or M-series.
- Google has had SafetyNet around for a while powered by ARM TrustZone, but is tightening the locks. Rooting your device invalidates SafetyNet, requiring complex workarounds that are gradually disappearing.
For the first time, remote attestation will no longer be a niche thing, only on some devices and not others. Within a few years, the amount of devices supporting remote attestation in some form will quickly approach 100%, allowing remote attestation to jump for the first time from corporate networks into public networks. Remote attestation is a technology that doesn’t make sense when only 70%, or 80%, or 90% of devices have it – only when it reaches >99% adoption does it make sense to deploy, and only then do its effects start to be felt.
We’re already seeing the first signs of remote attestation in our everyday lives.
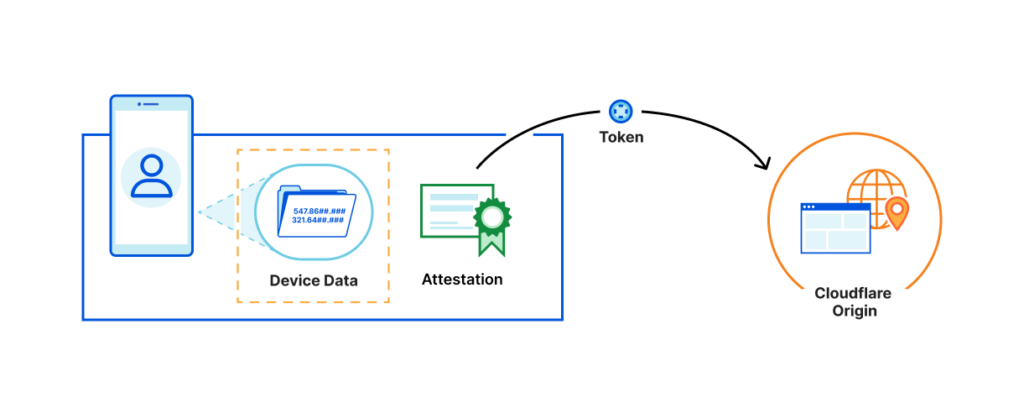
- macOS 13 and iOS 16 will use remote attestation to prove that you are a legitimate user, allowing you to bypass Cloudflare CAPTCHAs. How? By using remote attestation to cryptographically prove you are running iOS/macOS, without a jailbreak, on a valid device, with a digitally signed web browser.
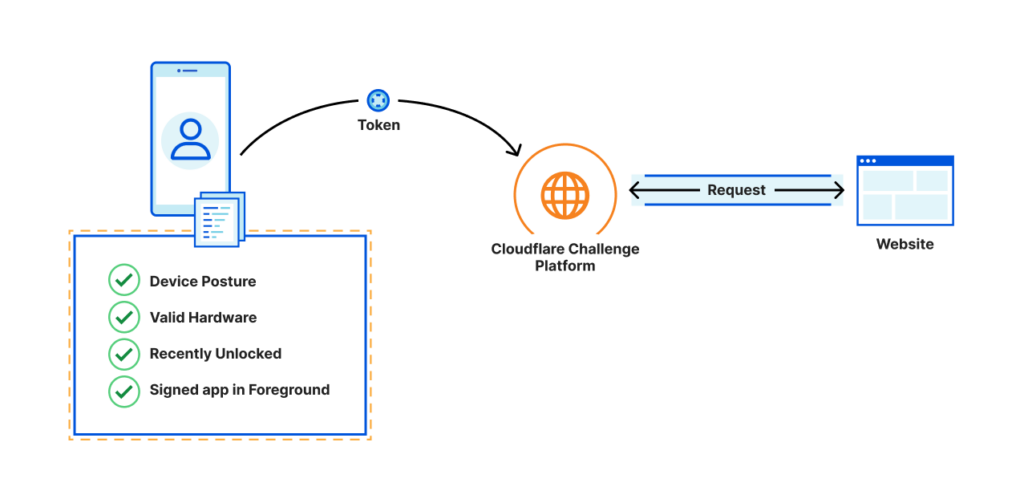
- Some video games are already requiring Secure Boot and TPM on Windows 11. According to public reports, they have not fully locked out users without these features, as they still allow virtualized TPMs, Windows 10, and so forth. However, they absolutely do not have to, and can disable virtualized (untrusted) TPMs and loading without Secure Boot as soon as adoption of Windows 11 and TPM is great enough. Once they shut the door, Windows 11 + Secure Boot + Unaltered Kernel Driver will be the only way to connect to online multiplayer, and it will be about as cryptographically secure against cheating as your PlayStation.
- Cisco Meraki powers an insane amount of corporate networks. Even in my own life, it was my school’s WiFi, my library’s WiFi, the McDonalds WiFi, even my grandparent’s assisted living WiFi. Cisco is also a member of the Trusted Computing Group that developed the original TPM and Remote Attestation to begin with. All they have to do, once adoption becomes great enough, is update their pre-existing “AnyConnect” app to use TPM/Pluton on Windows, DeviceCheck on iOS/macOS, and SafetyNet on Android/ChromeOS before you join the network. Anyone with an unlocked or rooted device need not apply.
I cannot say how much freedom it will take. Arguably, some of the new features will be “good.” Massively reduced cheating in online multiplayer games is something many gamers could appreciate (unless they cheat). Being able to potentially play 4K Blu-ray Discs on your PC again would be convenient.
What is more concerning is how many freedoms it will take in a more terrifying and unappreciable direction. For example, when I was in college, we had to jump through many, many hoops to connect to school WiFi. WPA2 Enterprise, a special private key, a custom client connection app, it wasn’t fun and even for me was almost impossible without the IT desk. If remote attestation was ready back then, they would have absolutely deployed it. Cloudflare has already shown it is possible for websites to use it to verify the humanity of a user and skip CAPTCHAs on macOS. What happens when Windows gains that ability? Linux users will be left out in the cold completely, as it is simply not practical to digitally approve every Linux distribution, kernel version, distribute a kernel module for them all, and then use the kernel module to verify if the browser is signed in the same way with all of its variations, without leaving any holes.
Thus, for Linux users, it will start with having to complete CAPTCHAs that their Windows and Mac-using friends will not. But will it progress beyond that? Will websites mandate it more? On an extremely paranoid note, will our government or a large corporation require a driver’s license for the internet, with a digital attestation binding a device to your digital ID in an unfalsifiable way? Microsoft is already requiring a Microsoft Account for Windows 11, including the Pro version. Will a grand cyberattack send deployment of this technology everywhere, and lock out Linux and rooted/jailbroken/Secure-Boot-disabled devices from most of the internet? Will you be able to use a de-Googled phone without being swarmed with CAPTCHAs and having countless apps deny access?
This is a major change of philosophy from the copy protection and DRM systems of yesteryear. Old copy protection systems tried to control what your PC could do, and were always defeated. Remote attestation by itself permits your PC to do almost anything you want, but ensures your PC can’t talk to any services requiring attestation if they don’t like what your PC is doing or not doing. This wouldn’t have hurt nearly as much back in 2003 as it does now. What if Disney+ decides you can’t watch movies without Secure Boot on? With remote attestation, they could.
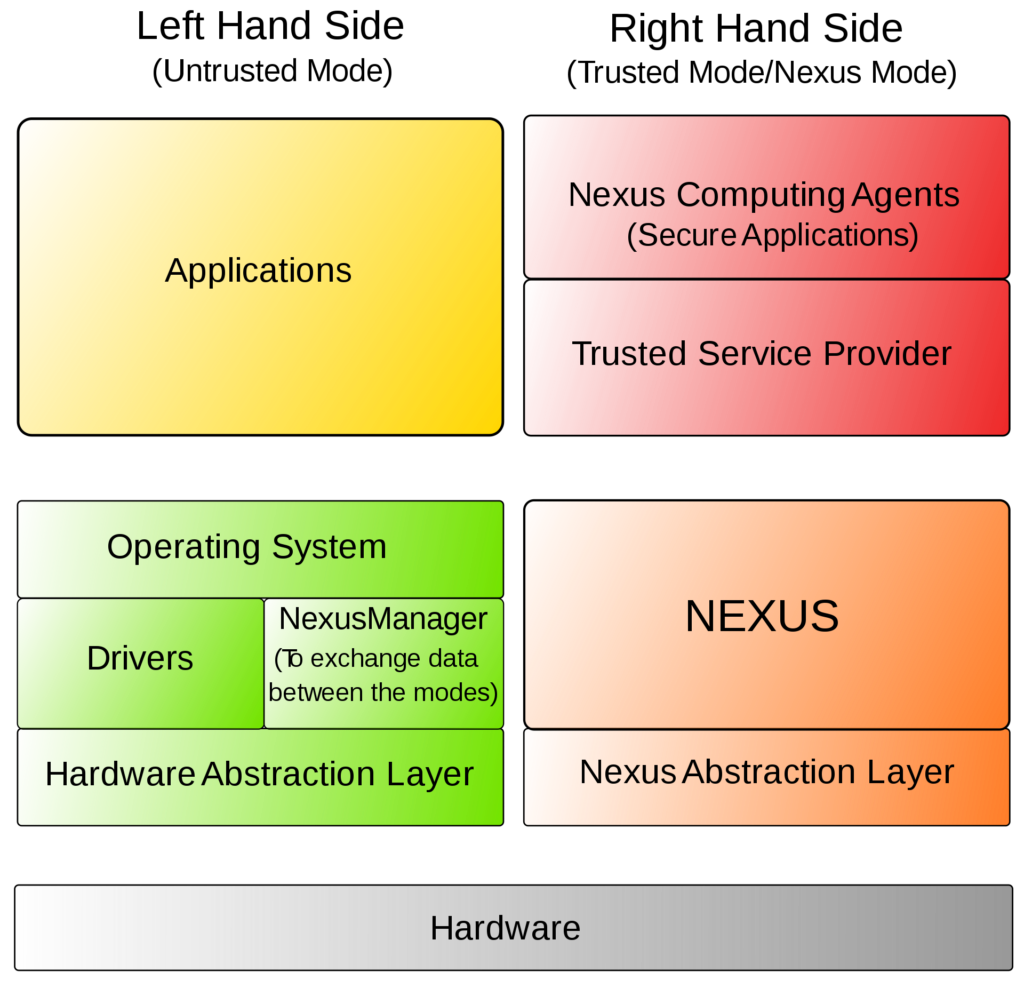
I think I’ll end with a reference to Palladium again, Microsoft’s failed first attempt at a security chip from ~2003, cancelled from backlash. It had an architecture that looked like this:
Now compare that diagram with Microsoft’s own FASR (Firmware Attack Surface Reduction). FASR is a “Secured Core” PC technology that is not mandatory yet and not necessarily part of Pluton, but very likely will be required in the future.
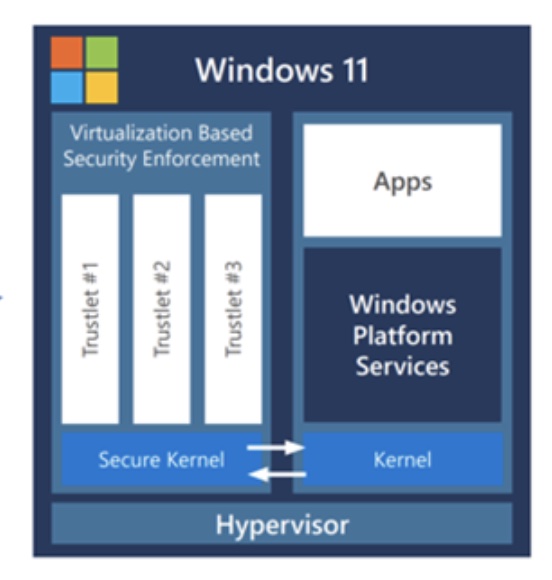
All they did was flip the sides around, have a hypervisor instead of separate hardware abstraction layers, and rename NEXUS to “Secure Kernel.” Otherwise it is almost entirely the exact same diagram as from 2003 that was cancelled from backlash. They just waited ~20 years to try again and updated the terminology. (Also, of note, is the use of the word “Trustlet,” plagiarized from ARM TrustZone which powers Android’s SafetyNet remote attestation system.)
Some things never change.

Hello,
When I read your bio it clicked as you reminded me of myself in college. So please take this in the light of an older enthusiast to a younger one.
When I was your age I saw the world as black and white but as I have gotten older I know that the truth resists simplicity. In this case it is important to understand why Microsoft is disabling third party certificates for secure boot and their new security processors. And that is a gand story of a ten Microsoft self own.
Back when secure boot realeased Microsoft was the only game in town if you didn’t want to update the uefi your self. This meant that market forces pushed everyone to get their code signed by uncle bill including threat actors. Fast forward 10 years and we see Microsoft signed malware. Oops so much for the security argument for secure boot with Microsoft keys.
So now they they need to move down the stack to maintain their status quo because they can’t cut bait with all their third parties without a huge hit to their bottom line.
I can’t give you details on what Cisco is doing in detail but I can tell you their network deployment is not what you described. They are also in a position where if they tried to stamp out Linux on their networks it would cripple the company. This isn’t uncommon in tech companies.
Something else that has changed from 10 years ago is that Linux nerds have positions of technical influence in the big tech companies. This limited how far the advocates of these anti-consumer folks can advocate.
The last thing I wanted to touch on is remote attestation and the folly of client side trust. In security we never trust the client however, the idea behind tpm and amp is that if I know what I am working with I can trust it. This just isn’t the case. Processes are easier to manipulate than most people developers want to admit. I suspect if we have this chat again in 2 to 3 years it will be in the light of companies writing blogs about how relying on client side trust was a bad idea.
remote attestation will not provide much or any additional security. If a technology already contains so many security holes before its introduction, this is usually not a good sign.
An overview of possible attacks can be found in this PDF: https://seclab.stanford.edu/pcl/cs259/projects/cs259_final_lavina_jayesh/CS259_report_lavina_jayesh.pdf